These days, developers push the boundaries of technology while creating modern cutting-edge applications. Users expect a smooth app with rich functionality that fulfills their needs. And most importantly they expect the application to be secure by default. A robust security foundation not only protects sensitive user data, it also safeguards the app’s overall performance and credibility.
This is precisely why we firmly believe that security audits should be an integral part of the app development process. Let’s dive deeper into the importance of security audits and see how they contribute to enhancing security capabilities when you plan to release a product.
What Is a Security Audit?
A security audit is an in-depth evaluation of the application’s codebase and infrastructure. It aims to ensure that software is protected against threats that could compromise its confidentiality, integrity, or availability.
A security audit assesses the efficiency of existing security controls. Namely, access controls, authentication and logging mechanisms, encryption methods, and more. Also, the process includes spotting areas that should comply with industry standards and best security practices. For these, you may want to use the following techniques:
- Penetration testing to simulate real-world attacks on an application, system, or network.
- Vulnerability scanning to scan the app and its infrastructure for any potential threats.
- Code analysis to examine the code structure to ensure all security features are in place.
On top of that, a security audit will provide insights and recommendations for improving the security of the software system. You will get a report with a detailed analysis of the identified vulnerabilities, along with recommendations to resolve them.
What Risks Can a Security Audit Identify?
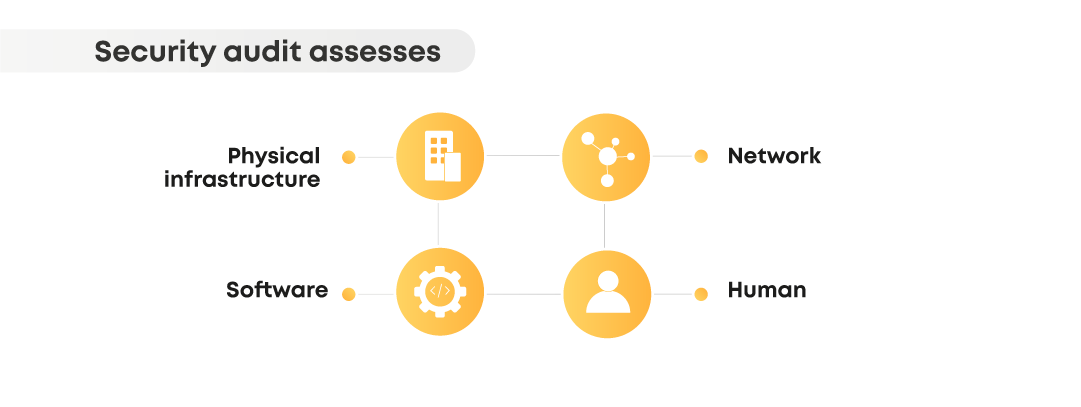
An effective security audit will help you spot common security risks. Generally speaking, it will assess an organization’s security controls relating to:
- The physical infrastructure and environment in which the system is housed.
- The software itself (including any security patches you’ve already implemented).
- Network vulnerabilities both internal and external.
- The human dimension of how employees handle sensitive information including its collection, sharing, and storage.
By evaluating each of these components, a security audit provides a holistic view of potential security risks, which may be associated with:
- Weak password policies. This includes weak or easily guessable passwords, password reuse, and a lack of two-factor authentication.
- Hardware failure. You will be able to detect whether servers, storage devices, or other critical hardware components are operating properly.
- Lack of system updates. Outdated software, applications, and firmware may contain vulnerabilities, which are known to cyber attackers.
- Inadequate network security. You will identify weaknesses in network security, such as unsecured wireless networks, open ports, and inadequate firewalls.
- Insufficient data backup and recovery plans. You will detect gaps in backup and recovery plans including a lack of off-site backups, inadequate testing, and incomplete recovery procedures.
- Gaps in employee training. You will get clues on weaknesses in employee training programs, as well as lack of policies and procedures, and insufficient access controls.
Business Benefits of a Security Audit
A security audit serves not only technical but also broader business goals.
- Provides an extra layer of protection that ensures your users’ sensitive data remains safe and secure.
- Enables to catch potential security issues early before they become major problems.
- Helps show users that you care about their safety and privacy, which will help build trust and loyalty.
- Saves money as resolving those issues after release involves costly fixes and damage control.
- Provide a thorough and documented record of the app’s security posture, which can be used for future reference.
- Ensure compliance with industry-specific security standards and regulations.
- Enhance the overall security posture of the app, which can lead to positive reviews, increased downloads, and improved revenue.
Steps of Integrating Security Audits into Application Development
We recommend considering a security audit as an integral part of the application development and maintenance. The auditing procedure is highlighted in our corporate application security checklist. The assessment of software for security usually involves the following key steps:
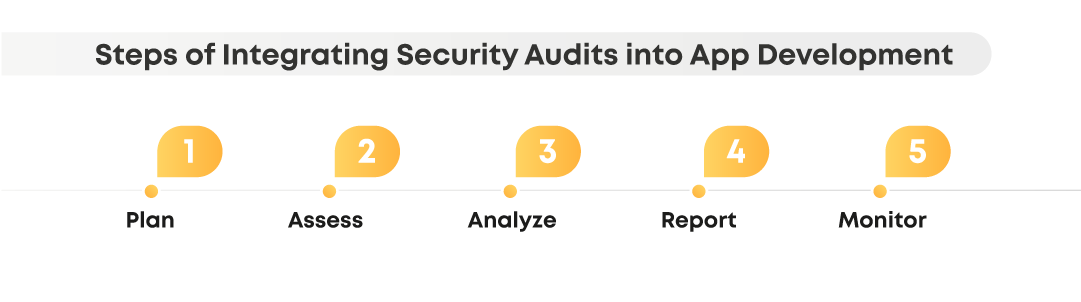
1.Plan. We define the scope of the audit, including the systems, applications, and networks.
2.Assess. Here we apply different testing and analysis techniques like vulnerability scanning, penetration testing, code review, configuration review, and others to spot any weak points in an app.
3.Analyze. As we get data on existing and potential security issues, we prioritize vulnerabilities based on severity, the likelihood of exploitation, and the potential impact on the organization.
4.Report. Our team documents the results in a report that includes an executive summary, detailed findings, and recommendations.
5.Continuously monitor. After an app goes live, we maintain its security to keep it resistant to emerging threats.
Summing It Up
We highly recommend incorporating security audits into your application development process to ensure the smooth performance of the final product and achieve the desired business outcomes.
Our team is dedicated to providing services that will help you avoid security risks in your production-ready software. We apply the best security practices that keep applications safe throughout their lifecycle. Get in touch with us to learn more about our process of security audits.





