Prioritizing the security of your web application and protecting against cyber threats is non-negotiable for today’s web app developers and owners. Recent research conducted by Verizon reveals that web application attacks contribute to 26% of all breaches, making it the second highest attack vector. Experts also point out that the most critical vulnerabilities often lurk within user authorization and authentication processes.
In this article, we’ll explore specific strategies and best practices for web application security. Whether you are a seasoned developer well-versed in web security or a beginner embarking on this journey, these insights will be your guide to build a more secure web application.

General Security Policy
Every web application comes with its unique security requirements, influenced by its particular type and purpose. For example, while fin-tech apps might demand more stringent protocols, e-commerce sites might have a different set of security priorities. However, there are some foundational security measures that can be applied universally to fortify your web application:
1. User password policy: Encourage users to create sturdy passwords, which ideally should be a blend of numbers, letters (both uppercase and lowercase), and special characters, spanning at least 10 characters.
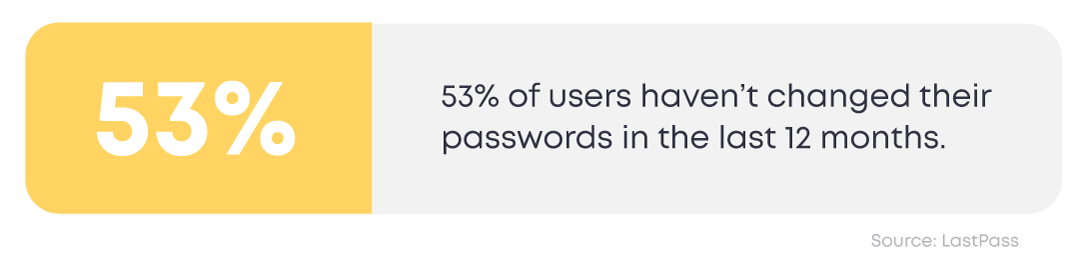
2. Password rotation: It’s wise to prompt users to refresh their passwords at regular intervals, say monthly or yearly, to diminish the odds of unsolicited breaches.
3. Two-factor authentication: 2FA provides an added security layer by confirming user identity using two distinct methods: something they know (like a password) and something they possess (like a verification code sent to their mobile). You can offer this feature as either a compulsory or an optional choice for users.
4. Logout timeout: Configure your application to log users out automatically after a specified duration of inactivity. This is particularly handy if a user misplaces their device or forgets it in a public space.
5. Login blocking mechanism: Introduce a mechanism that restricts the number of consecutive login attempts. If users surpass the stipulated number of incorrect logins—say, three times—the system could lock them out temporarily and dispatch a cautionary notification.
Incorporating these security measures, tailored to your web application’s specifics, can significantly amplify its defenses, enhance user trust, and thwart potential cyber-attacks.
Best Practices To Secure Your Web Application
To ensure the highest level of security for your web application, consider these nine strategies:
Update Your Libraries And Dependencies Regularly
In addition to implementing general security policies, another critical aspect of web app security is keeping third-party libraries and services up to date. This entails consistent monitoring for newer versions or updates from service providers and ensuring that your platform integrates these refreshed releases.
Here are some key reasons why regular updates are crucial:
1. Improved functionality and performance: By regularly updating libraries, you ensure your web application leverages the most recent functionalities, improvements, and resolutions for known issues. This not only refines its operational efficiency but also elevates the user interaction quality.
2. Enhanced security: Many updates carry fixes for identified vulnerabilities within third-party libraries. Overlooking these updates essentially creates an open door for cyber threats. Timely assimilation of these updates is instrumental in neutralizing potential security challenges and safeguarding user-specific information.
3. Compatibility and interoperability: Maintaining up-to-date libraries simplifies compatibility with other software components. This proactive approach diminishes the likelihood of unforeseen glitches, ensuring a smooth application runtime.
Keep API Keys And Credentials Separately
Separating API keys and credentials from the central repository is essential for maintaining security and adhering to best practices. By storing sensitive information in a separate and secure location, you can ensure the integrity and confidentiality of your data, consequently, minimizing the risk of data compromisation.
Furthermore, separating API keys and credentials also gives developers better access control. By maintaining a secure location, access permissions can be closely monitored, ensuring that only authorized individuals or systems can interact with sensitive data. This enhances the control and management of access rights.
Use Authentication And User Role Access
To ensure the security of your endpoints and routes, it is crucial to implement authentication mechanisms. One popular method is to use JSON Web Tokens (JWT). In this approach, each request includes a JWT token that is validated by the backend server to determine if the user has access to the requested resource. It is important to authenticate all endpoints except for publicly accessible ones, such as the login, register, and forgot password pages, since the user is not logged in at that stage yet.
Moreover, we can use role-based authorization. This allows you to assign different roles to users and specify their access privileges. For example, it ensures that one user cannot access another user’s data; or that a Customer cannot access data meant for Administrators only. This adds an extra layer of security and protects sensitive information from being accessed by unauthorized users or roles.

Encrypt Sensitive Data
If your web application stores or collects sensitive information such as social security numbers, driver’s license numbers, payment information, etc., it’s best to keep that information encrypted. In that case, even if attackers manage to steal some information, they won’t be able to decrypt it without a secret key.
Furthermore, instead of storing passwords as plain text, it is recommended to hash them using a one-way hashing algorithm. This process converts the password into a unique string of characters that cannot be reversed or decrypted. This way, even if an attacker gains access to the database, they will not be able to get the original passwords.
Implement HTTPS
Incorporating HTTPS into your web application guarantees data confidentiality by encrypting user information and providing a secure and private communication channel. By implementing HTTPS, you build trust with your users and assure them that their sensitive data is transmitted securely over the internet.
HTTPS offers several other benefits, including:
- improving SEO rankings (search engines prioritize websites that use HTTPS)
- defending against man-in-the-middle attacks
- complying with data protection regulations
- enabling essential browser features like geolocation services, access to device cameras and microphones, and push notifications
- strengthening the authentication process, making sure that users access only legitimate and trusted websites.
Validate Data Input
Validation helps prevent malicious input, data errors, and potential vulnerabilities. By implementing proper validation techniques, you can ensure data integrity and protect your app against attacks like SQL injection and cross-site scripting (XSS).
It also enhances user experience by prompting users to enter valid data. This helps minimize errors and leads to a more seamless and reliable user experience.
Ensure System Integrity Through Errors Handling
When a server-side error occurs during a request, ensure that users are not able to view the complete stack trace. They should only receive a message about what went wrong. Displaying the entire stack trace can give attackers a clue about the libraries or services used. So, make sure to address each error and provide users with suitable messages that do not compromise the security of the system.
Do Auditing
In a web application, incorporating regular auditing and logging is crucial for various reasons. Firstly, it provides a detailed record of system activities and user interactions, which offers valuable insights for troubleshooting, debugging, and diagnosing errors. Moreover, auditing and logging play a crucial role in strengthening security measures and helping timely identify and respond to potential breaches.
Run Penetration Tests
A penetration test, also known as a pen test, is a simulated cyberattack against your web application or system to check for any critical vulnerabilities and security weaknesses. While this might come with an attached cost, if you’ve got the budget, it’s an investment that pays off significantly. As of 2023, the global average cost per data breach amounts to 4.45 million U.S. dollars. To conduct a penetration test, a dedicated team of security specialists will test your web application and infrastructure and give you tips on how to fix identified issues. It’s recommended to run a pen test from time to time as new features are implemented.
To Sum Up
By implementing these practical measures, you can strengthen your web app’s security and ensure that your users are satisfied with using the product.
Should you wish to elevate your web app’s security, our experienced team is here to guide and support you. With our comprehensive technical know-how and the right resources at hand, we can create web applications that stand robust against potential risks. Let’s embark on this journey together.





